SSH (Secure Shell) is a network protocol that provides a secure & encrypted channel to log into remote servers or computers to run commands and administrate the destined machine.
In simple words, it works on a client-server architecture and encrypts a tunnel between a local client and a remote server, normally on port 22. Thus, sensitive information (passwords and commands) is encrypted so eavesdropping is not possible.
Prerequisites:
- You must have a logged-in server IP address.
- Username to remotely log in. (Commonly ‘root’ for Dedicated and VPS servers)
- Password to access your server.
- Ensure your IP is allowed in the firewall and SSH access is enabled.
- SSH client installed on your computer (e.g., PuTTY).
Steps to log in to your server by SSH using PuTTY:
Step 1: Open PuTTY on your computer.
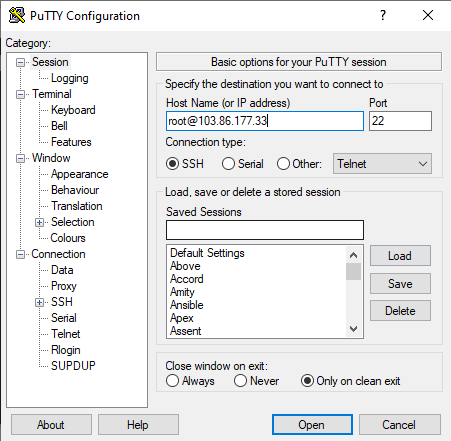
Step 2: In the ‘Host Name (or IP address)’ field, you can either enter the hostname or the IP address of your server. You can also directly enter the provided username. By default, the port is always 22. (Ensure what port has been configured by your system administrator or provider to avoid glitches.)
Enter it in the field ‘Port’ and hit the ‘Open’ button.
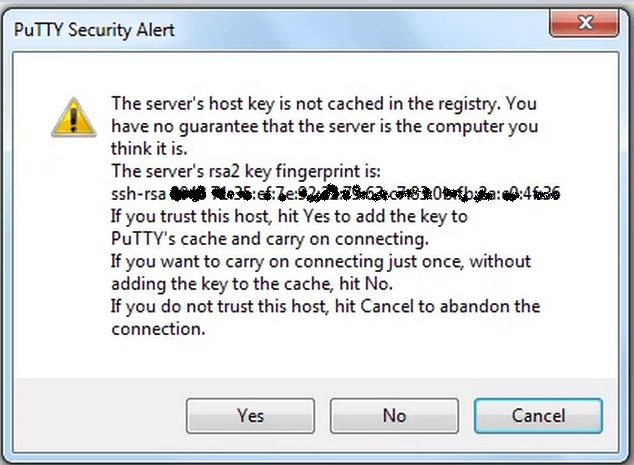
Note: If it’s the first time you are logging in, the “PuTTY Security Alert” might pop-up. Close the popup by just clicking the option ‘Yes.’
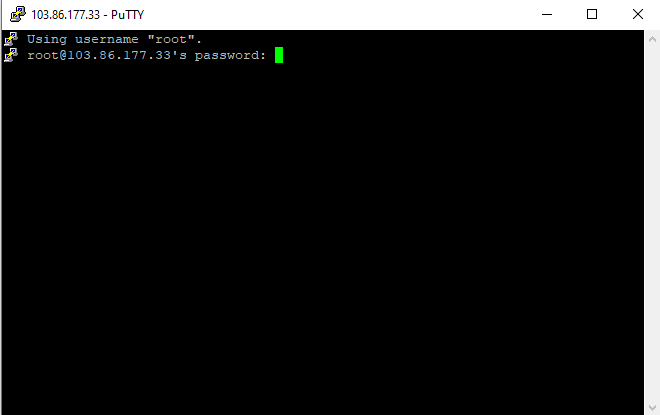
Step 4: If you only typed in the server’s name or IP address, the server will then ask you for your username. When prompted for ‘login as:’, here you have to enter your username.
Step 5: Now the system will prompt for your password. Simply enter the password and hit the ‘enter’ button on your keyboard.
That’s it! If your username and password were correct, you’ll be logged in and see a command prompt that looks something like this:
[root@test ~]#This indicates you’re now connected to the server and can start typing commands.
Remote management using SSH on your server opens up secure access. With this easy-to-follow guide, you can now break through the complexity barrier and access and manage your server securely with ease through an encrypted channel. Experience the convenience of secure command-line administration!








