SSH (Secure Shell) is a crucial element to secure remote server management. It enables you to connect and control your Linux VPS using encrypted communication. Such encryption secures sensitive data, keeping it out of the reach of cybercriminals.
However, since SSH operates on the default port 22, it often becomes a prime target for brute-force attacks. The simplest way to boost your website security is to change the default port, making it hardware for automated threats to find and exploit your server.
In this tutorial, we’ll walk you through changing your SSH port step by step—helping you choose a secure new port without interrupting access to your server.
Choosing an SSH Port Number
It should be chosen from an unused port to avoid potential conflicts and reduce security threats on your VPS. Some of the most used port numbers and protocols along with their respective services are listed below:
| Port Number | Service | Protocol |
| 20 | FTP (data transfer) | TCP |
| 21 | FTP (control) | TCP |
| 22 | SSH | TCP |
| 23 | Telnet | TCP |
| 25 | SMTP | TCP |
| 53 | DNS | TCP/UDP |
| 67/68 | DHCP | UDP |
| 69 | TFTP | UDP |
| 80 | HTTP | TCP |
| 110 | POP3 | TCP |
| 123 | NTP | UDP |
| 137/138/139 | NetBIOS | TCP/UDP |
| 143 | IMAP | TCP |
| 161/162 | SNMP | TCP/UDP |
| 179 | BGP | TCP |
| 389 | LDAP | TCP/UDP |
| 443 | HTTPS | TCP |
| 636 | LDAPS | TCP/UDP |
| 989/990 | FTPS | TCP |
| 3306 | MySQL | TCP |
| 8080 | Alternative to HTTP (web) | TCP |
| 8443 | Alternative to HTTPS (web) | TCP |
Also, select a port that is not in the standard well-known range (0-1023) and the registered ports range (1024-49151). It is advisable to use a non-standard port from the dynamic or private ports range (49152-65535).
How to Change the Default SSH Port?
As you have chosen the new port, let’s understand the different steps to implement the change.
Access your server via SSH
Access the server securely before you make any changes. Follow these steps to connect SSH through your server.
For Windows, macOS, or Linux, start by opening a new terminal window. On Windows, you may need an SSH client like PuTTY.
Use this command to login to your server. Replace the username with your real server username and server_ip with your server IP address:
ssh username@server_ipEnter the login credentials you provided. For enhanced security, it is recommended to use SSH keys instead of passwords.
Edit the SSH configuration file
After you successfully access your server, the next step is to modify the SSH configuration to use a new port. It involves editing the sshd_config file, that controls several parameters of your SSH daemon.
Use the following command to open the SSH daemon configuration file in the nano text editor:
sudo nano /etc/ssh/sshd_configScroll down until you find the line that includes #Port 22. This line is commented out by default, and the number 22 represents the default port.
Remove the # to uncomment this line and change 22 to your desired port number, such as 61189.

Adjust Firewall Settings
You need to adjust the firewall settings to allow traffic on the new server after updating the SSH port. However, if you have never configured any of them, skip this process and proceed.
This is how to update firewall rules by using Uncomplicated Firewall (UFW):
Run the following command to open up incoming connections on your new port using TCP. Make sure to replace 61189 with the port you are going to use:Lastly, restart UFW for changes to take effect:
sudo ufw allow 61189/tcpReload UFW to apply the changes:
sudo ufw reloadUsing either method, verify the current UFW status by running the following command:
sudo ufw statusIf you are installed any other firewall on the server you need to allow the port in the firewall.
Restart the SSH service
After you have modified the SSH configurations and the firewall settings, the next step is to restart the SSH service so that the new alterations can take place.
For systemd based systems, which are used by default in newer distributions such as Ubuntu, Debian and CentOS, restart the SSH service using the following command in the terminal:
sudo systemctl restart sshdYou can use this command for older systems that use SysVinit.
sudo service ssh restartAfter the restart, check the SSH service status to see if everything is working.
sudo systemctl status sshdVerify the New Port
Since you have restarted the SSH service, the next thing to do is check that SSH is running on the new port. You must verify that our changes were successful and that you can access the server.
You can use either ss or netstat to check an SSH portIf you have ss, here is the command you can execute to check all of your active connections, along with filtering for your new SSH port:
ss -tuln | grep [new_port_number]The output may look like this:

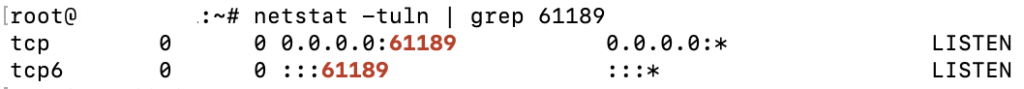
In case you don’t like to use the ss command, you can always just check with the netstat command:
netstat -tuln | grep [new_port_number]And the output will look similar to:
Log in using the new port
To test connecting to the server with the new SSH port number, open a new terminal window and execute the following command:
ssh -p new_port_number username@server_ipPlease replace new_port_number, username, and server_ip with your specific information.
The new port must be used for SSH connections to confirm that your server is functioning correctly.
By changing the default SSH port, you can reduce your server’s vulnerability to attacks.
In addition to using firewalls, updating server packages regularly, and setting up multi-factor authentication, you can make your SSH server more secure by implementing this change.
It is important to remember that security is an ongoing process that benefits from regular attention and adaptation.








