The deception website warning is seen when hackers access your website and upload malware on it. Google doesn’t accept any of its web users to access your site and spread the malware any further. This is the reason, Google Safe Browsing hits your site with a ‘deceptive site ahead’ notice.
Meaning of ‘Deceptive Site Ahead’
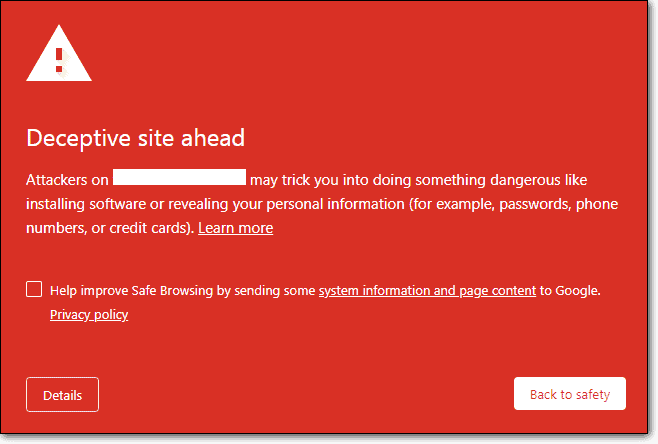
Basically, ‘deceptive site ahead’ is a warning message (the message appears on a red background) given by Google on sites that are found to be unsafe for visitors to browse on their devices.
Below are Google’s thoughts on what it says your website is ‘Deceptive’:
- There are phishing pages hosted on your website.
- The website is infected with malware/virus.
- Some code on your website is linking to questionable websites as per Google.
- Your visitors’ personal information is transmitted to unsecure servers/links through your website.
- Your website’s code contains a credit card stealing malware.
What are the Reasons to get the Deceptive Site Ahead Warning on your website?
Phishing and malware are the two major reasons for Google displaying a website’s deceptive or fake warning. But, there are many other reasons too. Below are the mains reasons to get a ‘deceptive site ahead’ warning:
1. Phishing
A website that screens itself as a legitimate source and misleads innocent users to reveal sensitive personal information like credit card details, passwords, credentials, etc. Phishing is an illegal way to fetch personal account details by hackers. One can execute phishing by using several maneuvers like:
- Adding legitimate-looking pages on the website that cheat the users for adding their personal information like phone number, credit cards, and emails.
- Injecting viruses or keystroke loggers (which record what you type) and giving away your passwords/usernames to the hacker without your knowledge.
- By displaying seriousness and needing prompt action at your end. Have you heard about a situation wherein the victim is being told that if you do not give your bank credentials instantly, your bank account will be hacked? Yes, you got that right, it is phishing.
A legal bank or any other institution would not force you to make a decision by asking you to fill some random form online.
2. Malware
Malware, the short form for malicious software is another reason for Google flagging a website as deceptive. Malware is the next key reason for the ‘Deceptive Site Ahead’ warning. Websites are many times infected with malware for months until it is found. A Malware is often inserted into a website with below frequent cyber attacks:
Cross-Site Scripting (XSS) Attack: Cross-site scripting attack is used as a way to add a malicious link that automatically downloads on a user’s computer when visited. There are several plugins, themes and websites that are vulnerable to XSS. Many times it is seen as the ‘low hanging fruit’ of web security because several websites are vulnerable to it. This can prove to be a quite hazardous attack when combined with other vulnerabilities. Therefore, Google blacklists those sites giving the deceptive warning.
SQL injection Attack: Using SQLi you can add, modify, and delete records in the database. This type of content is called a malicious payload and is an important part of the attack. When this content is sent by the attacker, malicious SQL commands get executed in the database. Therefore, Google blacklists a website. Further, it might also get added to your website via vulnerability in your CMS (eg. WordPress, Magento, OpenCart etc.) theme, or plugin. You might come across a situation that your website was trying to load harmful scripts on visitor’s site.
Malicious Advertisements (Malvertising): In case Google finds redirecting ads, random pop-ups, or malware loading ads on your website, it displays the deceptive warning to save your users from getting cheated to visit malicious websites.
Such ads can infect visitors directly without the need of any action from them. They don’t even need to click on it to infect them. Therefore, it becomes a tough situation. Hence, Google displays the deceptive site ahead warning in this case.
Not Having Proper SSL Certificate: Remember Google is very strict with its policies. Recently Google has made it compulsory to have an SSL certificate installed on their websites and also announced that SSL would be important for website ranking.
There are sites that have been flagged as ‘deceptive’ as they didn’t move from HTTP to HTTPS. It is not just enough to install an SSL certificate but you also need to redirect your website from HTTP to HTTPS. Also, if some of your web pages have HTTP and some have HTTPS, Google gets a mixed content signal. For this reason, your website can be flagged by Google.
Confirming If Your Website Shows Google Chrome Deceptive Site Ahead
It might be that you don’t see the Google Chrome browser warning for “Deceptive Site Ahead” when you search for your website.
Many business owners are warned by their regular customers or third party about the warning message. This is serious as your customers are at risk because they are sharing their personal information with you.
You can check if your website really has a Google Chrome deceptive site ahead warning with the below ways:
- Browse your website from another computer.
- Visit your website from incognito mode.
- See if you have received a security notification from Google Search Console in your email.
- Check your website status in Google Safe Browsing for a warning message.
- Check if you have received any security notifications in Google Search Console.
Basically, the first and second methods are enough to verify. The other three methods can be used if the first two don’t work.
Checking Google Safe Browsing for a Deceptive Site Ahead Warning
In case your website receives a deceptive site ahead warning on it you will get notified from Google Search Console.
What if you haven’t set up the Search Console?
It will take time to set it up correctly, upload the sitemap, and wait for Google to analyze the links. So, it is better to check your site in Google Safe Browsing for a deceptive website warning.
But with Google Safe Browsing you won’t be able to analyze the extent of the damage caused to your website or it won’t give you the solution to resolve the deceptive site ahead warning.

Checking Google Search Console for Security Notifications
On your Google Search Console dashboard, go to the Security tab:
Head to the infected pages:

You will get a list of all the affected pages and list down the actions you’ll need to take next to resolve the damage done to your website.
Steps to Remove the Deceptive Site Ahead Warning
Step 1: Find the Damage Done to Your Website
Login to your Google Search Console, go to the Security tab and go to the infected pages section as mentioned above.

In the ‘Detected Issues’ section, click on ‘Learn More’ and understand where the infection is:
- On a page? (Eg.: blog.example.com/pages/page1.php)
- In a particular group of pages? (Eg.: blog.example.com/pages/)
- In some post? (Eg.: blog.example.com/post1/)
- In the entire blog? (Eg.: blog.example.com/)
- In the complete domain or subdomain? (Eg.: example.com)

In the screenshot above, you can see that the wp-content folder contains some dangerous files.
Once you evaluate the damage, it will help you fix the situation quickly and efficiently.
Then check the date when suspicious content was discovered by Google. The exact dates can be seen next to the URLs listed in the ‘Detected Issues’ section of the ‘Security’ tab.
You won’t get more information from Google Safe Browsing and other online malware scanners on how to resolve deceptive site ahead warning. When you know the time of the received message, it will help you to check the actions you took right before that date. Did you install a new theme/plugin or update a plugin?
NOTE: It’s not always the perfect way to find malware. There are instances where malware is inactive for a while before it starts to show actual symptoms of a hack.
So, in case it doesn’t help, you can try to ‘Fetch as Google’ for those infected pages to understand what went wrong:

This will help you know more about the core problem. Next, you will need to remove the malware from your website.
Step 2: Remove the Malware
It is not easy to remove the malware from your website, so don’t take it lightly. If you take any wrong action, it will completely destroy your website.
But you will need to remove the malware from your website for fixing the “Deceptive Site Ahead” notice from it.
Below are two ways to do this:
- Use a WordPress security scanner and cleaner to clean your website.
- Manually clean your website (This is not recommended).
If you have good knowledge about manual methods of cleaning then only take the risk of cleaning your website manually.
Steps to Clean Your Website using WordPress Security Plugin
We highly recommend you to install a WordPress security scanner rather than using online malware scanners to remove malware from your website. The reasons are as below:
- Google Safe Browsing can just detect the activity of malware on your website and not its location. It won’t help you to remove the malicious code either.
- Are you skilled in PHP, HTML, Javascript, and Database Management? In case you aren’t, you will find most of the malicious scripts and ads exactly the same as regular code.
- If you understand coding and the way websites work would you be able to give time to check all the files and database tables on your website for malicious code and third-party scripts and remove it?
Simply speaking, don’t take the risk of removing the malware on your own unless you’re an expert at it. It’s a bad idea and it can completely destroy your website.
Steps to Clean Your Website Manually (NOT RECOMMENDED)
Remember that it isn’t a good idea to clean your website manually. We don’t recommend it in any situation.
However, if you know the risks and still want to remove the malware manually, you need to understand that cleaning a hacked website includes 4 steps:
- Scan files on the server to check for malicious code;
- Scan the database tables to check for malicious commands;
- Search backdoors and ghost admin accounts;
- And finally, remove the malicious without disturbing the website.
If any website is hacked, you will find the indicators of a hack. Now, we will check the indications of a compromised website and try to remove the malicious code that comes with them.
Before starting, ensure to take a full backup of your website. In case anything goes wrong with your website, this backup will help you get back on track.
#1 Scan files on the server to check for malicious executable code
Hackers insert malicious code at two places — the files on the website and its database tables. First, let’s check for files because they can contain third-party scripts.
Note that most modern malware is much complicated as compared to a single file with only malicious code on it. Many times, you’ll find the malicious code inserted into important files on the website.
Check for files with suspicious names in the below folders.
- wp-content
- wp-includes
These folders should not contain any executable files. If you find any PHP files here, then that’s a bad thing.
You might notice that Google or other online malware scanners flag Javascript files as the malicious code.
If this is true, Javascript particularly injects content into the frontend. In simple words, Javascript can’t execute malicious activities on its own. A PHP function or code snippet is needed by the malware to execute Javascript.
So, if you are wondering “how to get past deceptive site ahead,” then you should clean up the PHP code that initiates the malicious Javascript.
#2 Look for Malicious String Patterns in the WordPress Core Files
WordPress core files comprise essential code that helps in the normal functioning of the website. Therefore, it’s a good place to hide malicious code.
Recognizable patterns called ‘String Patterns’ are left by most malware that you can search for. Check for them in the below files:
- wp-config.php;
- .htaccess
- wp-activate.php
- wp-blog-header.php
- wp-comments-post.php
- wp-config-sample.php
- wp-cron.php
- wp-links-opml.php
- wp-load.php
- wp-login.php
- wp-mail.php
- wp-settings.php
- wp-signup.php
- wp-trackback.php
- xmlrpc.php
Check for the below snippets:
- tmpcontentx
- function wp_temp_setupx
- wp-tmp.php
- derna.top/code.php
- stripos($tmpcontent, $wp_auth_key)
These are PHP functions commonly used in malware and it would be good to start investigating from it.
Note that functions are not bad. Their purpose is to expand functionality in normal code.
If it isn’t possible to find if the code is malicious or not, it clearly indicates that you should not be deleting it. It would be better to hire a WordPress security expert or install a WordPress security plugin.
#3 Clean Hacked Database Tables
It is not easy to fix databases, but those can be cleaned. Go to the cPanel and open up phpMyAdmin to access your database tables.
It is recommended to follow the below steps only when cleaning your database:
- Log in to phpMyAdmin.
- Take the backup of your complete database.
- Find spammy keywords and links that can be seen on spam comments.
- Open the table containing suspicious content.
- Remove any suspicious content manually.
- Test to verify the website is still working after changes.
It is strictly recommended to only make one change at a time and test the effects of the change before changing anything else in your database.
If there is something slightly off on your website, restore your database from the backup you took immediately.
#4 Remove Backdoors Embedded in Your Website
To check for backdoors is the worst part of manual cleanup. Small code snippets that enable a hacker to regain access to your website even after cleaning it up are called as backdoors.
It is hard to find backdoors because they are generally hidden in regular code too.
Search for the below PHP functions on all your files:
- base64
- str_rot13
- gzuncompress
- eval
- exec
- create_function
- system
- assert
- stripslashes
- preg_replace (with /e/)
- move_uploaded_file
Remember these aren’t evil functions by default, and many plugins and themes use them legally too.
Step 3: Submit A Review Request
It isn’t enough to only clean up your website. It is important to remove all the malware from your website and then tell Google about it for reviewing your website and removing the warning message.
WARNING: Before submitting a review request with Google, ensure that your website has no traces of the malware present anywhere on it. In case your website is still infected, your request will be rejected by Google to fix the deceptive site ahead warning message from your site. If you get rejected by Google for number of times, it will tag you as a ‘Repeat Offender’ and you won’t be able to request a review for 30 days.
Submitting multiple review requests for the same issue is also a bad idea. After submitting a review request at once, wait for 1-3 days for Google to sort it out. If you submit multiple requests it will take more time and in certain cases, Google may tag you as a ‘Repeat Offender’.
Step 1: Navigate to the Security Issues tab for requesting a review of your code from Google Search Console.

Step 2: If you have fixed the issue, click on the “Request Review” button.
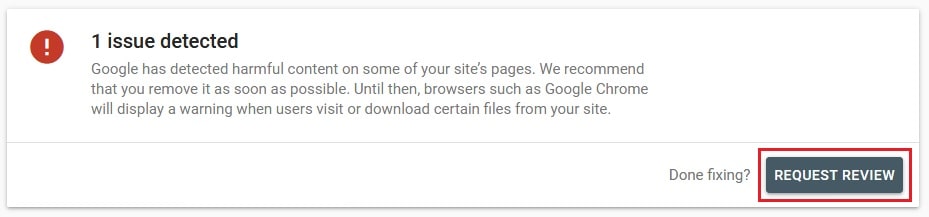
Step 3: Mention all the actions taken by you in the input field. When you mention the actions in details, it will be clear to Google and better for your application. Next, click on ‘Submit Request’:

Step 5: At last, click the Manual Actions section.

Step 6: Follow the 1-4 steps again to resolve all the security issues on Google.
Ensure to follow the above steps to remove ‘deceptive site ahead’ notice.








