Distributed Denial of Service attacks or DDoS attacks pose a significant threat to websites and online platforms often disrupting their working and eventually leading to major service outages. These types of attacks flood the servers with excessive traffic making it almost impossible for authorized users to access the targeted website resulting in potential outages. So, are you wondering what is DDoS protection all about and why it matters? It refers to a variety of advanced safety measures that help identify, mitigate, and block disruptive traffic spikes, making sure that your website is always up and running without affecting your online presence.
With the advancement of modern cyber threats, it has become crucial to know how to implement successful DDoS strategies for safeguarding your assets. In this blog, we’ll familiarize you with the fundamental concept of DDoS protection, offer proven techniques to protect your online assets, and train you with the knowledge on how to fight off this harmful cyberattack.
If you want to know more about DDoS protection, or how to mitigate the denial of service in cybersecurity, this post has all the answers for you.
Table Of Content
What is a DDoS Attack and What are its Types?
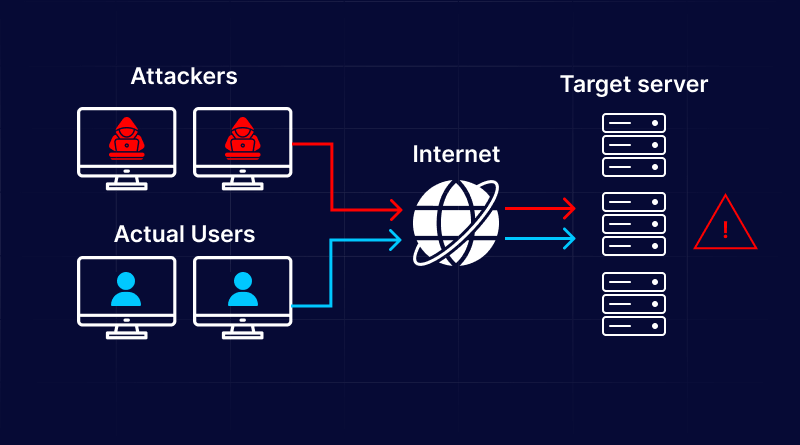
A Distributed Denial of Service (DDoS) attack is an orchestrated attack that aims to overload an intended server, network, or service with a tremendous amount of internet traffic which disrupts normal operations.
This kind of attack derives its strength from the help of numerous infected machines like computer devices, IoT gadgets, and other connected devices to overwhelm their targeted systems with malicious traffic surges.
You can think of a DDoS attack as an unexpected massive influx of traffic, making it impossible for regular customers to reach their destination.
Key Types of DDoS Attacks
A variety of DDoS attacks are available and attackers often use multiple techniques to weaken their victims. These denial-of-service attacks usually focus on one of the seven critical network layers of the Open Systems Interconnection (OSI) model.
Just like different departments in an organization, every layer in the OSI model has a distinct role. The cyber attackers select their target layer depending on the asset they want to disrupt.
The DDoS attacks are broadly categorized into the following 3 types:
- Volumetric (Gbps)
- Protocol (pps)
- Application Layer (rps) Attacks
As all these three types fall under the DDoS category, they often lead to confusion or are interchanged unintentionally. In a few instances, to make things worse, these DDoS attacks can even overlap in a single attack leading to more serious disruptions.
Cyber attackers frequently don’t restrict themselves to only one type of DDoS attack. Alternatively, they use a combination of volumetric, protocol, and application layer DDoS attacks in a single multi-vector assault with a single goal of hampering your business across different layers and multiplying the overall impact.
1. Gbps or Volumetric DDoS Attack
Most people will associate the term “DDoS” with the volumetric type of attack, simply because it’s the most popular. The first volumetric DDoS made headlines in late 1990 and has since birthed an army of copycats.
Volumetric attacks can also be called “floods.” It’ll flood a target’s server with requests; basically with unwanted pings and are measured in terms of bits per second (bps) or Gigabits per second (Gbps).
The concept behind a volumetric attack is easy: send the maximum amount of traffic possible to a targeted website to cause the server’s bandwidth to max out. Amplification techniques typically produce volumetric attacks. A common technique that attackers use to conduct a volumetric attack is DNS amplification. The illegitimate actor sends small DNS queries with the fake source IP address to a DNS server. When the request reaches the server, it sends a heavy response back to the victim.
Attackers also build volumetric attacks using botnets consisting of exploited IoT devices. The connected devices mostly don’t have basic security defenses but being Internet-connected and executable, they can be easily manipulated.
With such cheap IoT devices as toys, small appliances, thermostats, security cameras, and Wi-Fi routers, an effective attack is launched with a few clicks. A hacker can easily take advantage of the limitless reach of the web to launch a successful volumetric DDoS attack with the help of very minimum resources.
The Mirai botnet is the devastation of what leveraged and unsecured IoT devices can result in. The Mirai used to target the IoT devices as each infected one joined a volumetric DDoS attack against some of the world’s biggest organizations.
2. PPS or Network Protocol DDoS Attack
An internet protocol is a distinct set of rules through which information exchange across the internet happens. The best-known TCP/IP is the most prominent among the sets of rules for requesting and transmitting data. The malicious attackers might take advantage of these weaknesses to seriously damage an online service.
Network Protocol DDoS attacks usually target layers 3 and 4 of the OSI model on network devices such as routers. They are measured in packets per second because they operate at the network layer.
Some examples of DDoS attack types operating at the network layer include:
- UDP Floods
- SYN Floods
- NTP Amplification
- DNS Amplification
- SSDP Amplification
- IP Fragmentation
- SYN-ACK Floods
For Example:
The ping of death (POD) is an IP fragmentation attack based on the size limitation inherent in the packet. Using parts of a packet or fragments, the exploit can overflow memory buffers allocated for that packet and subsequently deny service to legitimate packets.
3. RPS or Application Layer DDoS Attack
Volumetric attacks and, to a lesser extent, protocol attacks break a service due to sheer volumes of requests. In contrast, application layer DDoS attacks or layer 7 attacks attack an edge server that serves up a web application.
These are more challenging to detect since attackers generally make requests just like normal users. These attacks therefore tend to present as smaller traffic spikes and do not necessarily rely on the presence of a botnet.
Application layer DDoS attacks are calculated in requests per second (RPS), in simple words, the number of requests generated by an application. In this regard, an application-layer attack is always a resource-based attack, therefore it requires much fewer requests to compromise an application. This is simply because the attack is on overwhelming CPU and memory, not bandwidth.
An application layer attack usually consists of hitting the web server, running PHP scripts, and contacting the database to load web pages. A single HTTP request, which is easy to carry out on the client side, can cause a server to execute many internal requests and load many files to satisfy the request, which slows the system.
An application layer attack can also be a multi-vector attack, which makes use of both volumetric and protocol attacks to enhance the possibility of taking a service offline. Multi-vector attacks are popular among cybercriminal groups due to their complexity and effectiveness.
| DDoS Attack Type | Metric | Category | Characteristics | Examples |
| Volumetric Attack | Data transfer rate calculated in terms of – Bits per second (bps), Gigabits per second (Gbps), flood | Connectionless | High volume, use bots | High volume, use bots |
| Protocol Attack | Packets per second (PPS) | Connection-based | Targets the network layer | Syn flood, ping of death |
| Application layer attack | Requests per second (RPS), low-rate | Connection-based | Challenging to identify | SQL injection, XSS |
The Process Behind DDoS Attacks
Distributed Denial of Service (DDoS) attacks are executed with the help of an interlinked network of devices across the internet. Such networks are comprised of computer devices and IoT systems that are affected by malware allowing cyber attackers to control them remotely. Each of these infected devices is recognized as a bot or zombie, whereas an entire network of these bots is referred to as a botnet.
After creating a botnet, an attacker can orchestrate the attack by remotely commanding every bot. When a botnet attacks the victim’s server or network, every bot bombards the target’s IP address with lots of requests, which can lead to overburdening the server or network and blocking access for regular users by causing a denial of service.
Additionally, identifying malicious traffic from genuine traffic is difficult because each bot works as an authenticated internet device.
Reasons for DDoS Attacks
The major intent behind DDoS attacks is to overwhelm or block authenticate traffic from accessing its targeted website by flooding it with harmful traffic.
For instance, DDoS attacks can block users from reaching a website, purchasing products or services, streaming videos, or interacting on social networking sites. Further, DDoS attacks can stop business operations, exhausting crucial resources or degrading performance, thus paralyzing business operations by preventing employees from accessing emails, and web applications, or carrying out regular business operations.
A Variety of Factors can Trigger DDoS Attacks
- Hacktivism: Hackers aim at companies or websites with different views or values to launch DDoS attacks against them. Therefore it is necessary to stay prepared for these kinds of cyber threats.
- Cyber Warfare: Governments use cyber threats such as DDoS to disrupt the critical infrastructure of an enemy state.
- Extortion: DDoS attacks are often used for blackmailing or extorting money from companies.
- Fun Purposes: Most attacks are committed by a few hackers who find it very entertaining to mess with stuff or try out cybercrime.
- Market Competition: These are the main examples of market competition motives. A business disrupts another by DDoS attacks to secure a competitive edge.
Understanding the Consequences of DDoS Attacks
DDoS is an attack wherein websites and online services can be disturbed in a few minutes, yet their impact reaches further. Thus, what real-world consequences result from these attacks, and how can businesses prepare? Let’s break it down.
1. Service Disruption
Disrupting services can be the most immediate effect of a DDoS attack. Within seconds after a DDoS attack, your website cannot be reached or has difficulties becoming accessible to the users, with very big losses due to wasted opportunities, angry clients, and loss of revenue. It takes only a few minutes of downtime to significantly affect the business of eCommerce.
Related: 6 Ways To Prevent Hackers From Touching Your Ecommerce Website
2. Damage to Reputation
An extended attack on one’s part exposes it to the public and might cause damage to your reputation as a business. Cases whereby clients’ confidence and trust are fully lost. It begins driving customers away and attracts some negative publicity.
3. Increased Operational Costs
Lessening the effects of a DDoS attack frequently calls for significant resources, leading to increased expenses. This might involve hiring cybersecurity professionals, upgrading existing infrastructure, or investing in stronger web hosting solutions. Without effective DDoS protection in place and with a manual approach, these costs can escalate dramatically.
Have you just started your business? Check out this significant Cybersecurity checklist for new business owners which will help you secure your website from malicious threats.
4. Performance Lag
Even after the attack has been receded, your website’s performance might still be affected. The DDoS attack can exhaust server resources, and slow down website performance and overall user experience, making it difficult to quickly restore normal website operations. Hence, slow and steady wins the race! This is not true for websites.
5. Loss of Income
For online businesses, especially in the eCommerce sector, one of the biggest consequences of having a DDoS attack is the loss of income. Each minute of lost business can translate to lost sales, abandoned transactions, and, ultimately, lower revenue.
6. Regulatory Compliance
Legal risks are, of course, the biggest issues for businesses operating in certain industries, especially if they handle sensitive customer information for example, banks and financial services. Failure to protect your platform against this type of attack might lead to litigation or penalties from regulating authorities, especially when a privacy breach or customer data compromise occurs. Therefore domain privacy protection is important.
7. Operations Disrupted
A DDoS attack has a way of impacting more than just the website. It may interfere with internal systems, deny employees access to some of the essential tools, and slow down the operation of the entire company. Lower productivity, in this case, is usually the intended outcome of these actions.
Why is it Crucial to Understand the Consequences?
Knowing the outcomes of DDoS attacks is a matter of awareness; it is also a matter of action. Understanding the wide-reaching effects on your business can serve as a step to getting prepared. A robust DDoS protection strategy needs to be in place to protect your operations from being severely affected and to ensure continuity.
How ready is your website for a possible DDoS attack? Take a look at this case study of the most authentic account of a massive DDoS attack that ever happened with GitHub in 2018. This is one of the most famous code repositories, which was attacked and reached its peak when it hit 1.35 Tbps and made the largest DDoS attack at the time.
Short-Term Impact:
- Service downtime: The platform was temporarily down, and users lost a lot of service across the world.
- Customer Impact: Developers experienced setbacks when accessing or committing code, which affected the business applications developed on GitHub collaboration.
Long Term Impact:
- Reputation Damage: While GitHub rapidly neutralized the attack, the sheer magnitude and severity put the entire security of the platform into question, especially given the cloud nature of the platform.
- Security improvement: In response, GitHub further improved DDoS protection, together with deploying a new traffic filtering system.
This case brings out the immense impact a DDoS attack can have on a platform, stressing the importance of DDoS protection in maintaining service continuity and reputation.
Are you concerned that your website could be an easy target for DDoS attacks? Check out Advanced DDoS Protection solutions offered by MilesWeb for your website right now!”
In this blog, we outlined the serious effects of DDoS attacks. With this knowledge in hand, you should now know what to expect and take precautions to protect your online presence.
What is DDoS Protection?
DDoS protection refers to the strategy and tools applied in order to avoid Distributed Denial-of-Service attacks, that affect the normal working of a server, service, or network. In such attacks, an effort is made to make a targeted website unavailable for use through heavy traffic flooding. Efficient protection against DDoS involves being proactive with respect to filtering out traffic, implementing rate limiting and specialized hardware, and using cloud-based services for malicious traffic detection. And then blocking unauthorized sources before the harmful flow reaches the system.
The dependable DDoS protection strategy could therefore mitigate a big attack while keeping your business online and without any downtime at all.
Core Elements of DDoS Protection
DDoS attacks try to overwhelm online services with heavy traffic loads for hampering the usability of the attacked website.
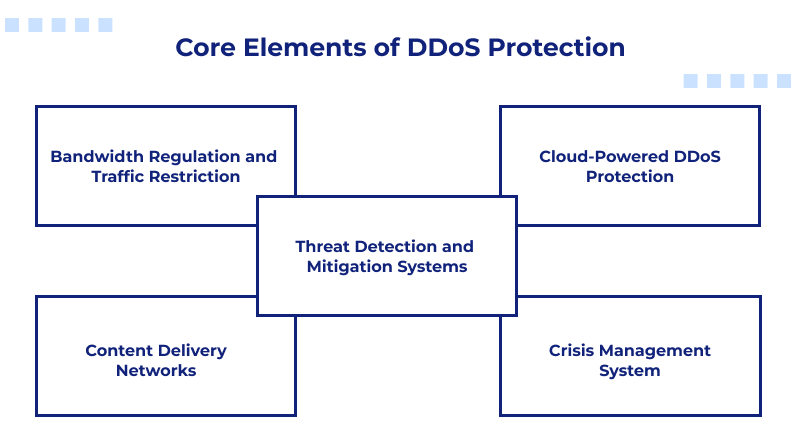
To protect your online websites from DDoS attacks effectively, a comprehensive protection strategy is necessary that covers the following key components:
– Bandwidth Regulation and Traffic Restriction
Filtering mechanisms to identify legitimate versus malicious traffic. Traffic restrictions are the mechanisms used to control the volume of traffic in the network to prevent network congestion.
– Threat Detection and Mitigation Systems
It utilizes IDPS that detects and stops malicious activity, such as DDoS attacks, by measuring the network’s response in the search for suspicious patterns.
– Content Delivery Networks
Distribute or place the content on multiple servers to absorb and mitigate the effect of DDoS attacks, enhancing service availability.
– Cloud-Powered DDoS Protection
Leverage cloud hosting services with scalable resources to deal with highly distributed volumetric DDoS attacks to ensure service continuity.
– Crisis Management System
An incident response plan should be prepared and continuously revised to respond quickly in a coordinated manner against the DDoS attack.
Essential Measures to Avoid DDoS Attacks
Recognizing the difference between normal traffic and compromised traffic is the major challenge in DDoS prevention. The DDoS threat can take many different forms in today’s cyberspace. The attack traffic comes in various forms such as, in conjunction, single source attacks to heavy and hard-to-detect attacks using multiple vectors.
A DDoS multi-vector attack is an attack in which many attack paths are used to overload a network with many different methods of attack, potentially delaying mitigation because of diversification.
Parallel attacks on several protocol layers together like DNS amplifier (targeting layers 3/4) combined with HTTP flood (targeting layer 7) are one of the multi-vector DDoS examples.
To defend against a multi-vector DDoS attack, various measures have to be taken because it is not a single point of focus. Usually, the more complicated an attack, the greater the chances of attack traffic getting deeply mixed up with normal traffic – the attacker aims to be as indistinct as possible, rendering mitigation efforts as ineffective as possible.
Investigations to stop or reduce traffic indiscriminately might skip good traffic along with the bad and the attackers might change and adjust their tactics to evade countermeasures. To successfully combat a sophisticated attempt at disruption, a layered solution will give the greatest advantage.
– Blackhole Routing
All network administrators have a solution through the use of blackhole routing methods. This method allows incoming traffic to follow a very slow and sometimes non-existent route, making it difficult or even impossible to use. In that way, they can minimize the potential danger.
According to the expert, the blackhole routing technique may come into existence when an ISP employs a method to mitigate a Distributed Denial of Service attack by throwing the traffic of the attacked website into the waste pipe. In this context, this method falls short as it facilitates the malicious actor to gain control over the network by blocking access to the network.
– Web Application Firewall
A WAF can be used to reduce the impact of a layer 7 DDoS attack. A WAF, by general definition, is placed in between the Internet and the targeted server. Serving as a reverse proxy, the Web Application Firewall acts as an intermediary for the targeted server, shielding it from some malicious traffic.
On the DDoS attacks layer 7, traffic from good and bad sources will be separated by the forward and the backward rules. Therefore, the layer 7 attacks can be hindered. A critical strength of WAF is the capability of promptly incorporating custom rules in reaction to the threat.
– Anycast Network Diffusion
This DDoS protection technique makes use of the Anycast network to disperse the harmful traffic across the distributed server network to reduce the excessive load. Similar to diverting a fast-flowing river into smaller streams, this DDoS protection strategy distributes the effect of the harmful traffic to lessen its intensity and neutralize destructive capacity.
The ability of an Anycast network to mitigate a denial of a service attack is determined by the attack’s magnitude and the network’s size and efficiency.
Importance of DDoS Mitigation Services
A distributed denial of service (DDoS) mitigation service is vital to making sure that services accessed online are available and performing well against cyber threats. With extensive strategies that detect, analyze, and prevent DDoS attacks, such services ensure that legitimate users of critical resources maintain continuous access. Efficient DDoS mitigation protects against likely financial losses and blemished reputation and can thus maintain user trust and confidence in an organization’s virtual infrastructure.
Last but not least, DDoS attacks are one of the persistent and dynamic threats to online services because they target availability, making such services unavailable to legitimate users due to overwhelming the systems with malicious traffic.
Deploying powerful DDoS protection measures is necessary in order to protect online systems from these attacks. Effective DDoS protection strategies consist of real-time traffic monitoring to identify abnormalities, implementing intrusion prevention tools to block harmful threats, and dispersing traffic using content delivery networks to efficiently handle traffic and neutralize attacks.
Moreover, by using cloud-based DDoS protection services offered by Milesweb, businesses can capitalize on easily scalable resources to mitigate massive attacks and maintain service continuity. With these DDoS protection measures, businesses can improve their capability to withstand these threats, ensuring continuous availability and reliability of online services.
FAQs
1. How to select the best DDoS protection solution for your business needs?
Consider a variety of factors such as the magnitude of possible threats, the volume of traffic you manage, monitoring in real-time, flexibility, scalability, integration ease, and affordability when selecting the perfect DDoS protection strategy. Also, select a solution that provides advanced threat detection, powerful defense strategies, and scalable infrastructure to guarantee uninterrupted service during massive large-scale attacks.
2. What are the charges for DDoS protection Services?
The cost of DDoS protection services differs based on various factors such as the security level, web hosting provider, and company size.
3. What are the regulatory challenges related to DDoS attacks that one must consider?
Regulatory challenges associated with DDoS attacks contain adherence to data security laws, guaranteeing continuous service, and following cyber security protocols. Businesses need to manage possible liability concerns, report breaches on time, and make sure that external providers abide by necessary rules and regulations.
4. What are the future developments in DDoS protection technology?
Cloud GPUs for advanced AI and ML for real-time threat detection, more sophisticated techniques for filtering traffic, seamless integration with 5G networks for quick response, and wide application of cloud-based solutions for flexible defense are some of the future developments in DDoS protection technology.